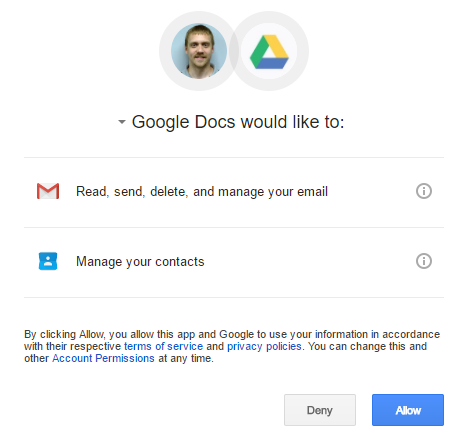
Just minutes ago I had a client forward me a copy of an email that they had just received. The email looked like a standard email that you receive when someone shares a Google Doc with you. The email was from an @gmail.com address. It contained a link to “Open in Docs” and the link was legitimate. When clicking on the link, the following page was displayed:
This is completely legitimate. Google has APIs available that allow developers to create apps which are able to integrate with Google’s services. One example of this is when you sign into a non-Google website and they offer to allow you to sign up using your Google account. If you’ve ever done this, you’ve seen the above page. You are granting an app developer access to specific data in your Google account. By clicking on the Allow button, the app developer can then access or perform any actions, as stated in the “Would like to” section of this prompt, on your behalf. Normally, this would be restricted to thing such as “See your email address” or very basic permissions. But in this case, as you can see, the requested permission is “Read, send, delete and manage your email.” In addition, the app is also requesting access to “manage your contacts” which means they will be able to read and delete your contacts. By clicking the allow button, you will be granting this third party developer the ability to send, read and delete emails through your Google account and access all of your contacts’ details that you have stored in Google Contacts (ie. if you have your phone synced with a Google account, this would likely include phone numbers, email addresses, birthdates, first and last names, and any additional info).
Let me re-iterate. The previous image is not malicious in and of itself. It is simply a step that Google requires in order to allow third party app developers to access your Google account data. Most of the time, this is harmless, but in this case, it is being used maliciously.
Now you may be wondering how I was able to tell that this was malicious. It looks legitimate. It shows Google Docs wants to access my account, it even has the Google Drive logo. What was the red flag that stood out? Firstly, Google already has access to all of your data. You shouldn’t be getting prompted to grant access to your account by Google except in cases where you are setting up a Google application on your PC (such as Google Apps Sync for Outlook or Google Drive Sync) which requires access to your account. Simply opening a Google Doc in your browser isn’t going to require any additional access because you are already signed into your account.
Secondly, if you mouse over “Google Docs” on this page (or any similar pages) you’ll notice that it becomes a clickable link. The arrow to the left of “Google Docs” also indicates that there is more hidden information. When you click on this app name, the following box is displayed:
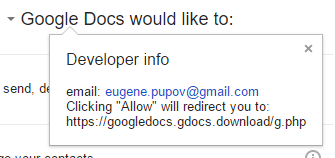 Now if we investigate this, you can pretty easily determine that this “Google Docs” app isn’t being published by Google. It is being published by [email protected]. A genuine Google application will actually show “Google” as the developer. And it also clearly states that by clicking “Allow” will redirect you to a specific URL. If you look closely at the URL, it is not a valid URL for Google. These two things told me that someone outside of Google is trying to gain access to my account.
Now if we investigate this, you can pretty easily determine that this “Google Docs” app isn’t being published by Google. It is being published by [email protected]. A genuine Google application will actually show “Google” as the developer. And it also clearly states that by clicking “Allow” will redirect you to a specific URL. If you look closely at the URL, it is not a valid URL for Google. These two things told me that someone outside of Google is trying to gain access to my account.
Not 5 minutes after the first client forwarded me a copy of the email, I had a user from another client calling me saying they had just gotten this email, opened it up and now the message has spread to everyone in the company and other users have also opened it up and granted access. Fortunately, Google had revoked this app’s OAuth access within minutes of this all happening, so the app no longer has access to anything and the developer will have to start from scratch and the account that was used will be banned from Google’s system. This makes it difficult for them to just start over repeatedly which is why you don’t see these type of attacks very often.
However, if you do end up victim of one of these attacks, or if you just want to see what 3rd party apps have access to your account (you’d probably be surprised) jump over to https://myaccount.google.com/permissions. If you don’t recognize something, or no longer use something that is still on that list, you can remove it. Doing so blocks all future access to your account by that app. This list also tells you exactly what permissions have been granted to the app and even when the app was originally authorized to have access to your account.
I hope you’ve learned something new today by reading this article and more importantly that it may help keep you protected in this crazy scary world of growing online threats. As always, if you have any questions, comments, or concerns, please leave a comment below and I’ll try my best to reply. Thanks for reading!